PWN - 'West Lake Challenge 2022' Writeup WP Reproduction
Getting into jail competition +1
Written before dinner, the rest has not been reproduced yet
babycalc
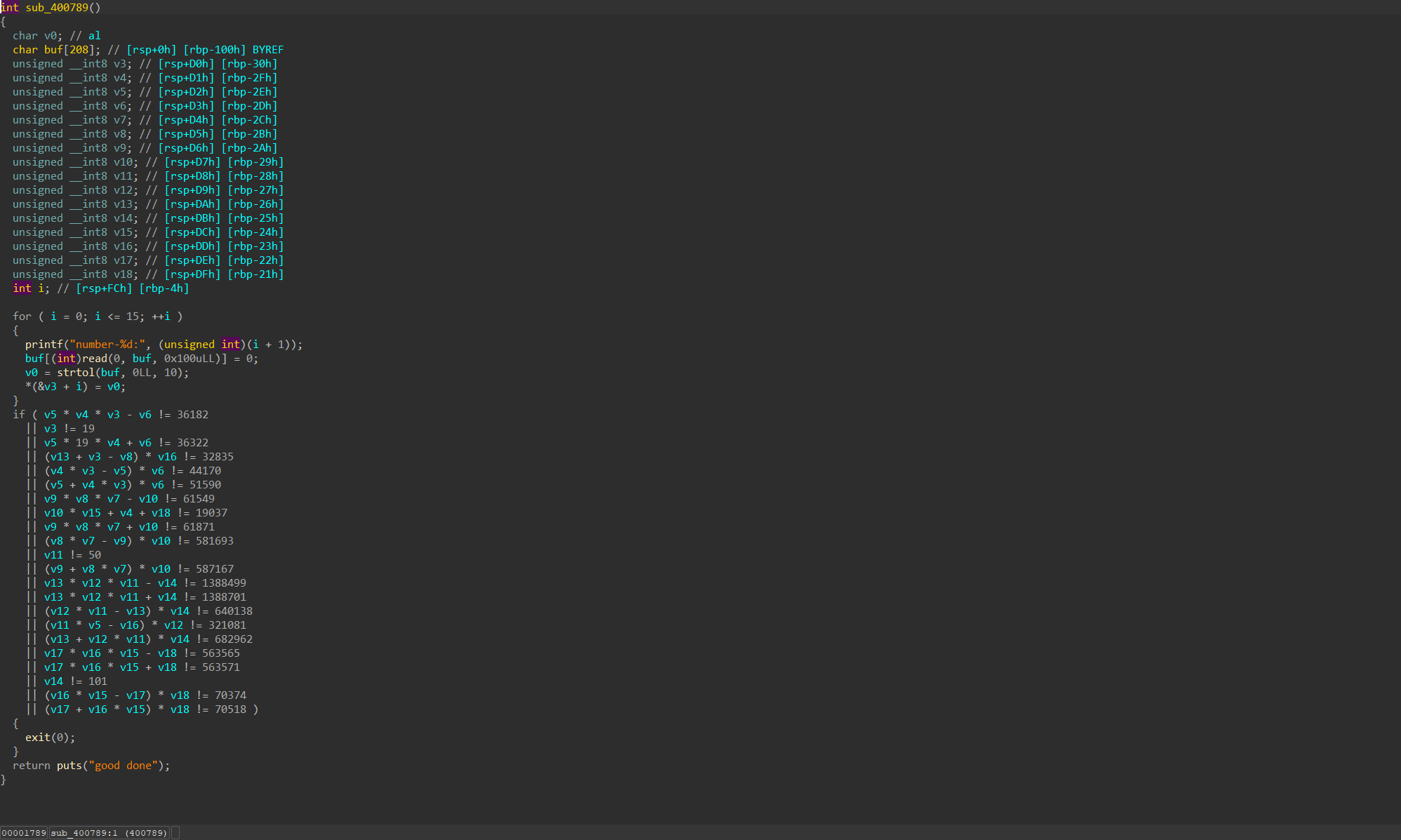
First, we need to bypass this decryption. We can use Z3 Prover for solving (so, anyone calculating manually? Ha ha, it's actually me)
Here, it can be noted that buf can overflow to modify the value of i, thus changing a byte's value. At the same time, here buf[(int)read], filling 0x100 bytes can overwrite the highest bit of rbp to 0.
Therefore, we can modify the last byte of the return address to return to another leave; ret, combined with modifying the last byte to perform stack migration.
Since the migration address is uncertain, we can fill the address of ret as slide code to increase the success rate (similar to filling shellcode with \x90).
Leak libc using puts for the first time, and then it is possible to trigger one_gadget or return to system for the second time.
The exploit was quite complicated to write.