「PWN」【DASCTF2023 Binary Specialization June】Writeup WP Reproduction
This PWN challenge is of high quality, but there were too many tasks and I was busy preparing for an exam, so I didn't spend much time on it. Here is a brief reproduction.
a_dream
This is a challenge involving stack migration in multithreading.
Key points:
- The sandbox opened by the main thread after creating a sub-thread does not affect the sub-thread.
- The stack of the sub-thread is allocated using
mmap, with the same offset as libc. - Both the sub-thread and the parent thread use the same GOT / PLT table.
Attack train of thought:
- Migrate the stack to
bss, and change thewritefunction's GOT entry to thereadfunction in the parent thread. - Utilize
putsto leak libc information, and then obtain the sub-thread stack address. - Perform ret2libc attack.
Points to note:
- After modifying the
writeGOT entry, we can only overflow by 0x10 bytes; however, at this point, the place ofrbp - 0x10coincides with the return address of thereadfunction. Therefore, we can control up to 0x20 bytes, which is enough to writepop rdi + got['puts'] + plt['puts'] + magic_read. - Even after obtaining the sub-thread stack address from the libc address,
magic_readcan still only overflow by 0x10 bytes, so we need to migrate to the high address of the stack.
Points of confusion:
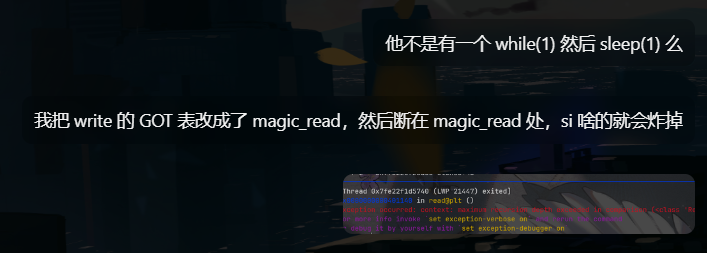
-
After modifying thewriteGOT entry, because thewritefunction is called every 1 second (waiting for stdin input), I'm not sure if it's a pwndbg issue or constantly being interrupted, so I can only break at that point. I can't usesi/n/c, as they will crash, making debugging very complex. Later on, I had to rely on continuously changing the breakpoint position to step through the code (laughs)Set GDB
set scheduler-locking stepto resolve this issue.
Exploit script (not suitable for remote, using local libc 2.35):
[Translated Python script...]